Feeless Crypto Wallet
- Self-custodial crypto wallet on iOS and Android
- 100+ coins and tokens, including ERC-20 and BRC-20 within a single multi-wallet solution
- Cutting-edge security of you assets based on multi-party computation
- Easy onboarding without seed-phrases and web3 difficulties
- Cloud backup of your wallet
- Feeless transfers
- P2P Swaps
- Farm-to-earn mechanics with on-chain points
GLOBAL PARTNERS
Powerful & Simple Wallet Solution
Spatium sets that bar as the most powerful wallet in the market while providing unmatched ease of use.
We have combined a set of unique features which enable the earning on crypto in a UX-friendly manner.
1/4
Easy Onboarding
Easy onboarding without seed-phrases and web3 difficulties
- Start using crypto in seconds
- Abstract away from all the crypto specifics
- Get the enhanced security of your assets
- Rely on MPC-TSS to get a safe and private key-free experience
- Select the way of creating wallet which fits you better
At Spatium, we envision a crypto experience as smooth and intuitive as popular Web2 applications. Our non-custodial wallet enhances this vision, emphasizing simplicity without compromising security.
Vasili Paulau, CEO at Spatium

2/4
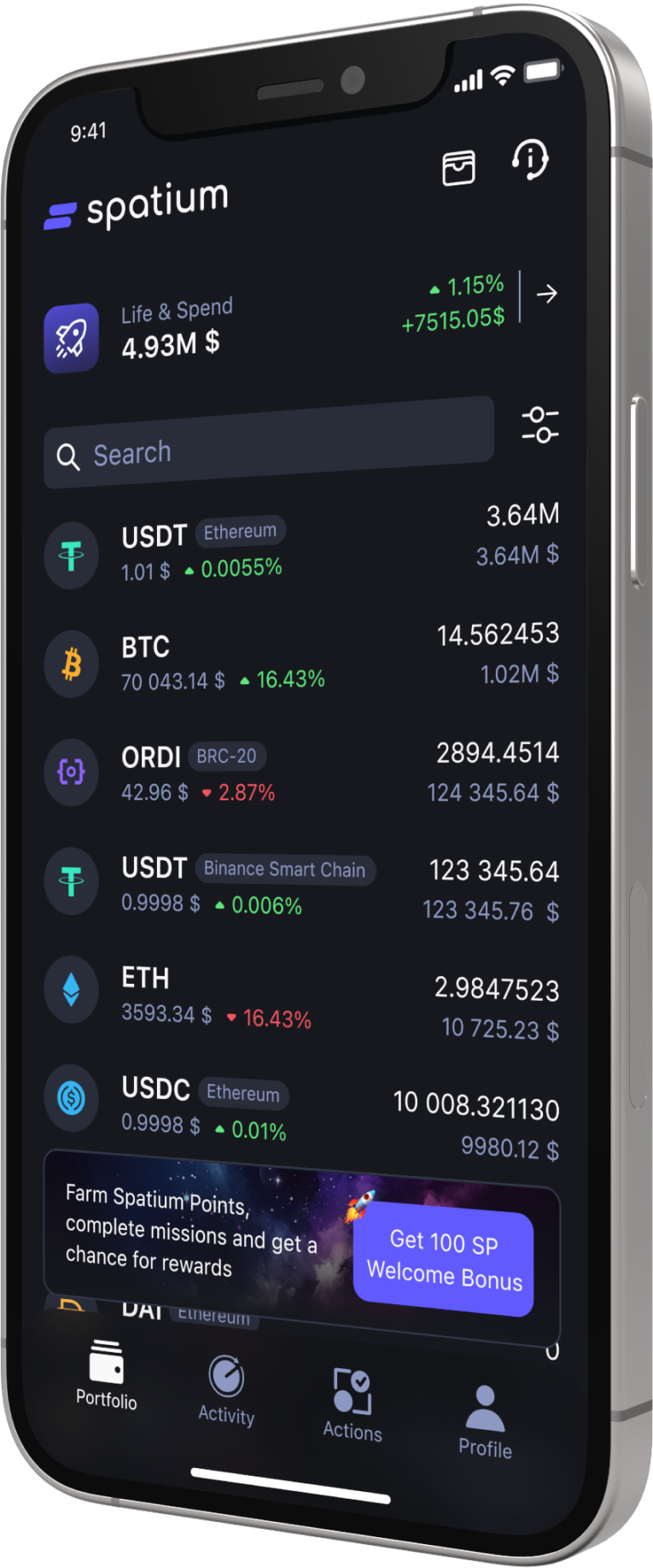
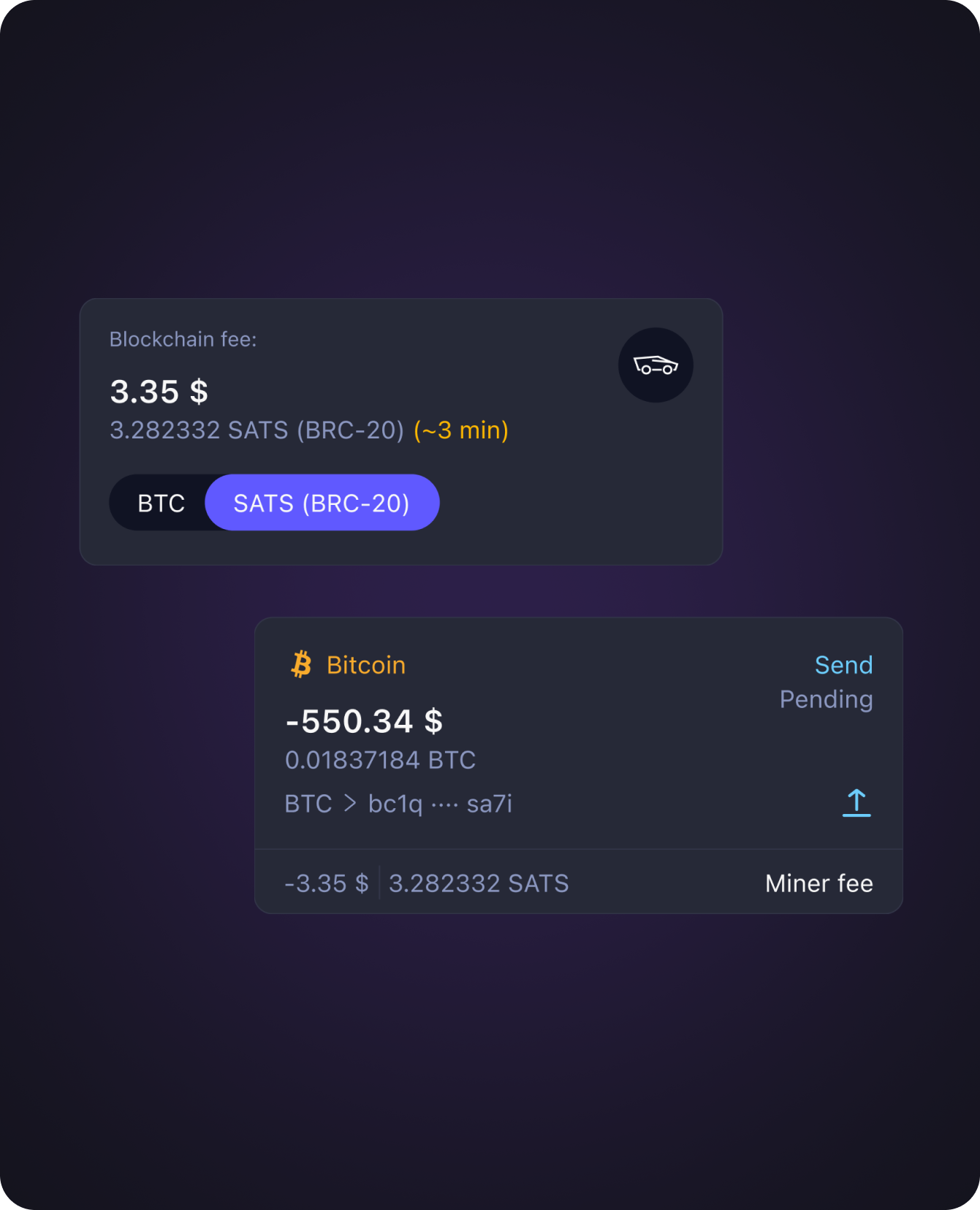
Feeless transactions
Pay blockchain fee in currency you send
- No more hussle in finding native coin to pay blockchain fee for sending transaction
- Spatium covers the fee. User pays in any currency
- Works with any blockchain
3/4
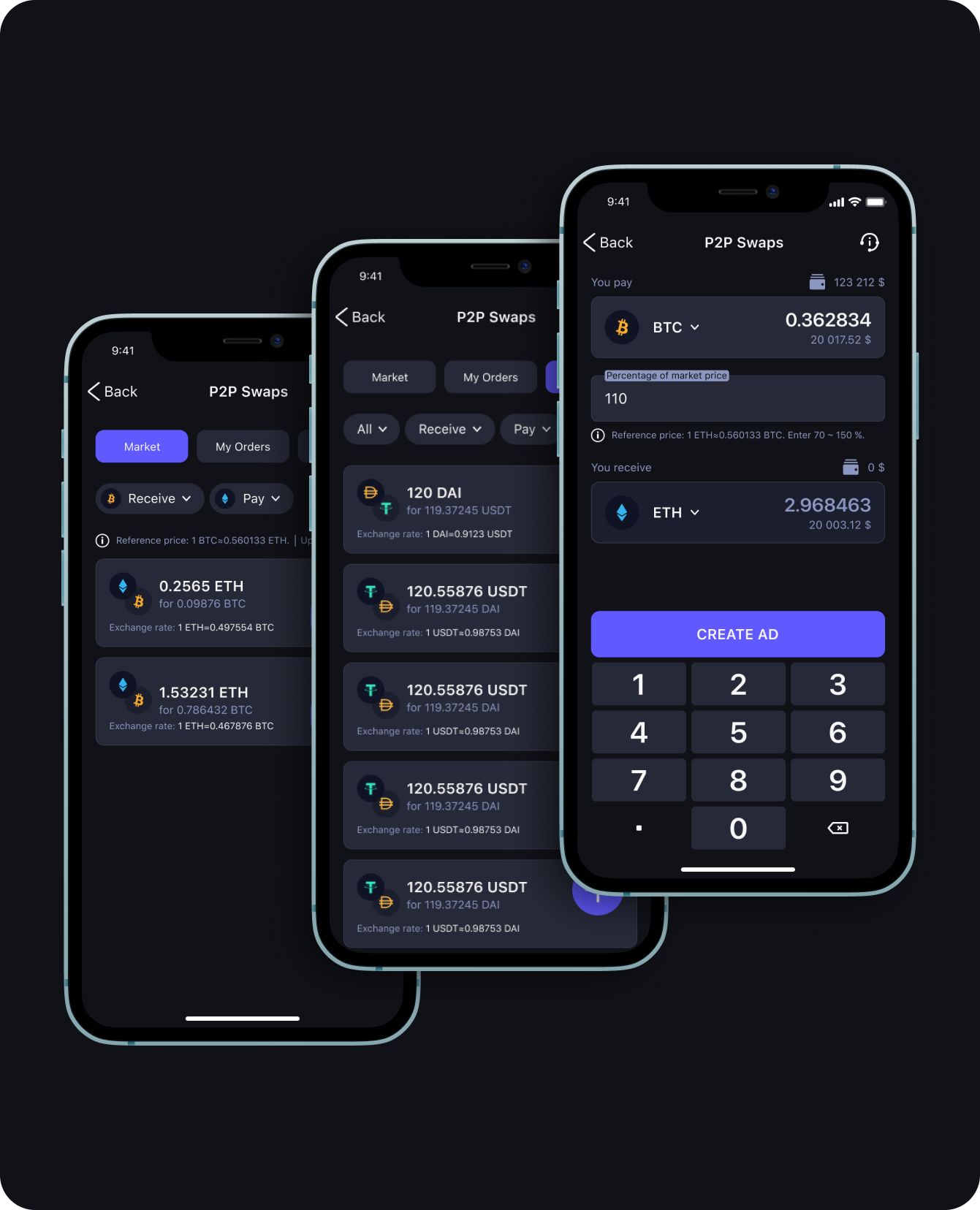
Cross-chain P2P Swaps.
Cheaper than ever
Closed Beta
Enjoy cheapest ever cross-chain P2P swaps guaranteed by MPC
- Perform P2P swaps in just two simple transactions from one user to another
- Lower fees cannot be imagined since no escrow is involved
- Lower fees than with DEX
- Safer than with CEX
- Security of the deal and your assets guaranteed by Spatium MPC
- Spatium does not take fee for P2P swaps
- Smooth entry to Bitcoin from any blockchain
4/4
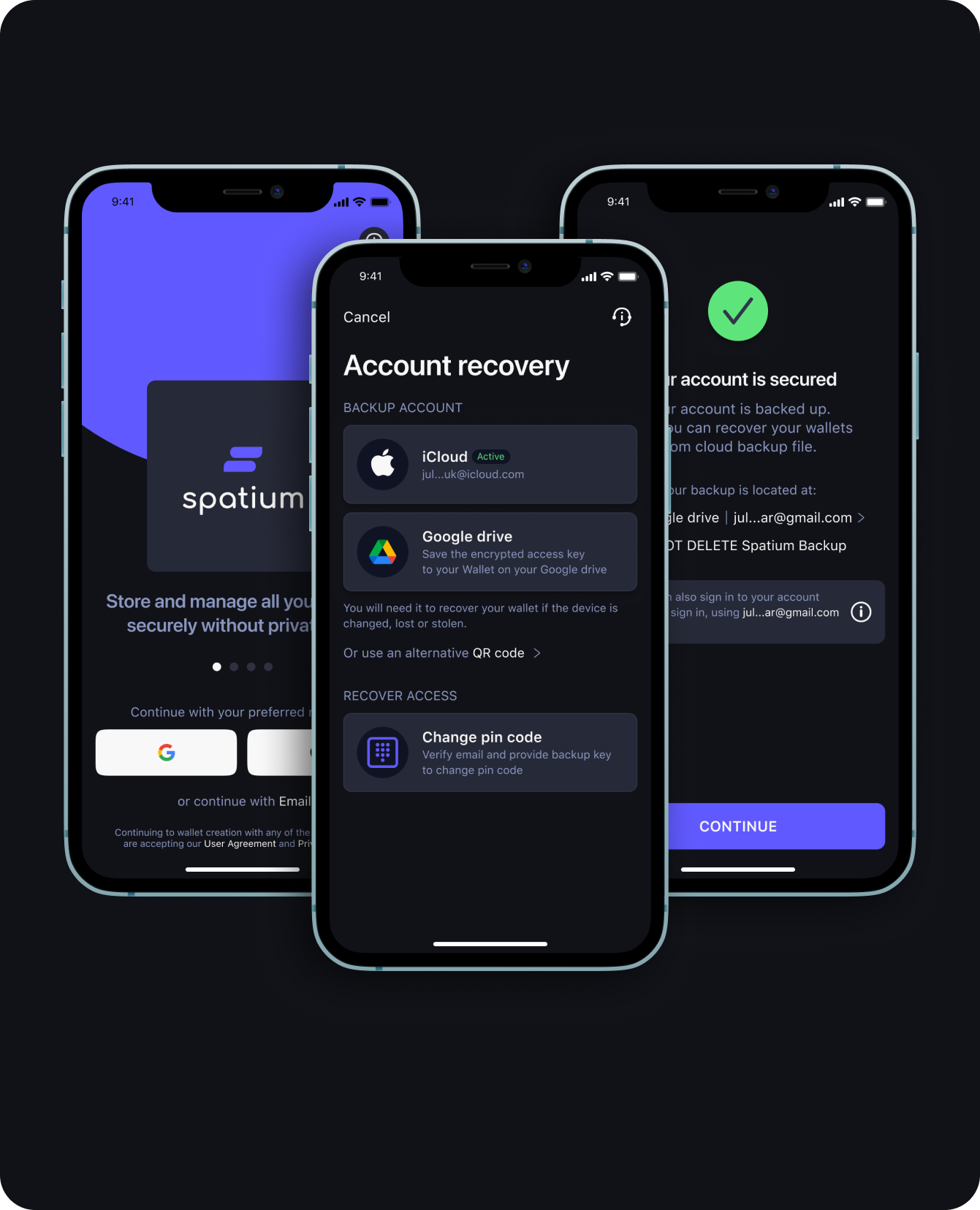
Cloud Backup
Secure your assets with encrypted cloud backup
- Save the encrypted access key to your wallet on your preferred cloud provider
- Restore the access to your assets anytime from your cloud
AND MUCH MORE
Spatium is the only solution you need to get simple access to crypto and web3 world.
Store, send, receive, buy, sell, swap cheaper than ever and earn - all you need in one simple and secure solution.
Multi-wallet
Manage your assets through multiple wallets within one account
Cross-Platform
Spatium is available on iOS and Android
Enhanced Security
MPC technology, 2FA, cloud and paper backups
Wallet Connect
Connect to any dApp via Wallet Connect
No private key difficulties
Farm-to-earn — earn points on-chain
Activity Notifications
Coming Soon
Spam Filters
Coming Soon
NFT & Ordinals Support
Coming Soon
Crypto Inheritance
Planned
Pre-built On/Off ramp
Planned
Earn Passive Income
Planned
Earn Spatium Points and Gain Real-World Benefits Join Now and — Don't Be Left Behind

🤑
Spatium Points are in-app on-chain gaming assets. The points hold potential real-world value.
⚡️
Download Spatium Feeless Crypto Wallet(Android, iOS) and start earning Spatium Points (SP) on-chain making very simple actions.
🚀
Don't wait—claim your 100 SP Welcome Bonus and embark on your space journey today!
Cutting-Edge Security for your Assets
Spatium is the team who first applied MPC cryptography to protect crypto assets in 2017.
We continue to put security of your assets without compromising convenience as our top priority.
Only you own and control your assets
Neither Spatium nor any other party have access to your assets, only you do
Spatium replaces the Private Key with two independently generated shards which together sign the transaction. Shard 1 is controlled by user, Shard 2 by Spatium. User always has access to Shard 2 for recovery purpose.
User always retain control and transactions are initiated based on his intent. Spatium acts as security guarantor and enables unique features making crypto simple.
Non-Custodial Wallet
Spatium is a non-custodial crypto wallet powered by multi-party computation (MPC) cryptography
MPC-powered Technology
We replace Private Key with a set of shards that are generated, stored and processed independently and never held in one place
No Seed Phrases
No need in complicated mnemonics such as seed phrases
MPC Scheme
Zero Trust - Highest Security
Planned
Spatium Becomes Better for You
Checkout our roadmap
Phase 1
-
MPC powered crypto wallet on iOS and Android
-
Easy login with Google & Apple
-
Cloud backup
-
Send & receive crypto
-
Feeless - pay network fee in currency you send
-
Chinese available
Phase 2
-
MPC P2P cross-chain swaps (crypto-crypto), no escrow and with lowest fees - closed beta
-
BRC-20 support
-
Feeless - more coins and chains available
-
Farm-to-earn — users earn points on-chain inside mobile wallet and get a chance for real value
-
Farm-to-earn — referral program
-
Farm-to-earn — tasks
-
Farm-to-earn — available as Telegram mini app
Phase 3
-
Crypto Wallet — available as Telegram mini app
-
More chains available
-
P2P swaps: public version, AML & wallet rankings available, enhanced security
-
Feeless - up to 30% network fee reduction
-
Rewards to Spatium users
-
Audits passed
-
Open source (Phases 1-2)
Phase 4
-
Buy & sell crypto
-
P2P swaps: fiat-crypto swaps, commission for swaps
-
P2P swaps and Feeless available in Spatium WaaS
-
Desktop version, browser extension
-
Web3 firewall
-
Staking available
-
Crypto inheritance
-
Audits passed
-
Open source (Phases 3-4)
Frequently Asked Questions
What is MPC used in Spatium?
Does Spatium take a commission for P2P swaps?
No, Spatium doesn’t take any commissions for any transactions, including Bitcoin and cross-chain P2P swaps. You only have to cover reduced blockchain fees you can pay in the currency you send instead of native network currency.
P2P Swaps Closed Beta Soon
How does Spatium reduce blockchain fees for cross-chain P2P swaps?
Spatium reduces blockchain fees for cross-chain P2P swaps in two ways. Firstly, for cross-chain P2P swaps Spatium guarantees the swap execution thanks to MPC, and there is no need in escrow. That said, a swap is executed in only 2 transactions instead of 4+ used by other products. The reduced number of transactions within a swap leads to fee reduction. Secondly, thanks to Spatium Feeless feature, in addition Spatium reduces blockchain fee up to 30% thanks to bundling up transactions. Moreover, thanks to Spatium Feeless feature users don’t need to have native chain currency to pay reduced fees but can pay them in currency they send. Thus, using Spatium P2P swaps users are able to save more than 30% on blockchain fees and pay them in the currency they send instead of looking for the native chain currency.
P2P Swaps Closed Beta Soon
Fee Reduction Coming Soon
How does Spatium MPC guarantee safe P2P swap execution?
Safe peer-to-peer (P2P) swap execution is enabled through Spatium MPC cryptography. Based on the fact that one of the secrets is stored on the Spatium server side, transactions are performed only after fast audit from the Spatium side. Spatium checks that the conditions of the swap are met and guarantees that assets of both deal participants will be sent.
P2P Swaps Closed Beta Soon
What is Spatium feeless feature?
Spatium feeless mode is a feature available for Spatium wallet users, which helps them to save on transactions up to 30% of the blockchain fees. It is applied for any type of transaction: sending crypto, Wallet Connect, P2P swaps, etc. Also, Spatium feeless mode allows users to pay blockchain fees not in the cryptocurrency of the network, but with the crypto type involved in the transaction.
Fee Reduction Coming Soon


MPC is a cutting-edge cryptographic technology that provides highest level of assets security and helps to eliminate the obstacles new users might have while operating crypto wallets, such as the use of seed phrases. MPC substitutes the private key (provides access to digital assets) with two (or more) secrets (shards). One secret is stored on the user’s device, the other on the Spatium server. The activation of these secrets helps to sign transactions and execute operations on web3.